Hi readers I am very please to announce you that I have just launched my new blog www.techlotips.com, This is the first time that I am blogging on a self hosted wordpress blog, Currently I am working on improving its design and optimizing it for search engines,I am using an Arthemia Premium theme by color labs project on this blog which is highly professional and seo optimized theme, In this blog I will write on following categories and topics!
1.IPhone Jailbreaking
2.PS Jailbreaking
3.Free Premium Themes
4.Search engine optimization
5.Getting Traffic to your blog
and much more!
I am looking for some guest posters too, If you have any suggestions regarding my new blog kindly tell me
Thursday, September 30, 2010
Monday, September 27, 2010
Hack a website using Directory Transversal attack?
What is root directory of web server ?
It is a specific directory on server in which the web contents are placed and can be seen by website visitors. The directories other that root may contain any sensitive data which administrator do not want visitors to see. Everything accessible by visitor on a website is placed in root directory. The visitor can not step out of root directory.
what does ../ or ..\ (dot dot slash) mean ?
The ..\ instructs the system to go one directory up. For example, we are at this location C:\xx\yy\zz. On typing ..\ , we would reach at C:\xx\yy.
Again on typing ..\ , we would rech at C:\xx .
Lets again go at location C:\xx\yy\zz. Now suppose we want to access a text file abc.txt placed in folder xx. We can type ..\..\abc.txt . Typing ..\ two times would take us two directories up (that is to directory xx) where abc.txt is placed.
Note : Its ..\ on windows and ../ on UNIX like operating syatem.
What is Directory Transversel attack?
Directory Traversal is an HTTP exploit which allows attackers to access restricted directories and execute commands outside of the web server's root directory.
The goal of this attack is to access sensitive files placed on web server by stepping out of the root directory using dot dot slash .
The following example will make clear everything
Visit this website vulnerable to directory transversal attack
This webserver is running on UNIX like operating system. There is a directory 'etc' on unix/linux which contains configration files of programs that run on system. Some of the files are passwd,shadow,profile,sbin placed in 'etc' directory.
The file etc/passwd contain the login names of users and even passwords too.
Lets try to access this file on webserver by stepping out of the root directory. Carefully See the position of directories placed on the webserver.
We do not know the actual names and contents of directories except 'etc' which is default name , So I have
marked them as A,B,C,E or whatever.
We are in directory in F accessing the webpages of website.
Lets type this in URL field and press enter
This will search the directory 'etc' in F. But obviously, there is nothing like this in F, so it will return nothing
Now type
Now type
So by proceeding like this, we we go for this URL
It takes us 5 directories up to the main drive and then to 'etc' directory and show us contents of 'passwd' file.
To understand the contents of 'passwd' file, visit http://www.cyberciti.biz/faq/understanding-etcpasswd-file-format
You can also view etc/profile ,etc/services and many others files like backup files which may contain sensitive data. Some files like etc/shadow may be not be accessible because they are accesible only by privileged users.
Note- If proc/self/environ would be accessible, you might upload a shell on server which is called as Local File Inclusion.
Counter Measures
1. Use the latest web server software
2. Effectively filter the user's input
It is a specific directory on server in which the web contents are placed and can be seen by website visitors. The directories other that root may contain any sensitive data which administrator do not want visitors to see. Everything accessible by visitor on a website is placed in root directory. The visitor can not step out of root directory.
what does ../ or ..\ (dot dot slash) mean ?
The ..\ instructs the system to go one directory up. For example, we are at this location C:\xx\yy\zz. On typing ..\ , we would reach at C:\xx\yy.
Again on typing ..\ , we would rech at C:\xx .
Lets again go at location C:\xx\yy\zz. Now suppose we want to access a text file abc.txt placed in folder xx. We can type ..\..\abc.txt . Typing ..\ two times would take us two directories up (that is to directory xx) where abc.txt is placed.
Note : Its ..\ on windows and ../ on UNIX like operating syatem.
What is Directory Transversel attack?
Directory Traversal is an HTTP exploit which allows attackers to access restricted directories and execute commands outside of the web server's root directory.
The goal of this attack is to access sensitive files placed on web server by stepping out of the root directory using dot dot slash .
The following example will make clear everything
Visit this website vulnerable to directory transversal attack
http://www.chitkara.edu.in/chitkara/chitkarauniversity.php?page=notification.php
This webserver is running on UNIX like operating system. There is a directory 'etc' on unix/linux which contains configration files of programs that run on system. Some of the files are passwd,shadow,profile,sbin placed in 'etc' directory.
The file etc/passwd contain the login names of users and even passwords too.
Lets try to access this file on webserver by stepping out of the root directory. Carefully See the position of directories placed on the webserver.
We do not know the actual names and contents of directories except 'etc' which is default name , So I have
marked them as A,B,C,E or whatever.
We are in directory in F accessing the webpages of website.
Lets type this in URL field and press enter
http://www.chitkara.edu.in/chitkara/chitkarauniversity.php?page=etc/passwd
This will search the directory 'etc' in F. But obviously, there is nothing like this in F, so it will return nothing
Now type
http://www.chitkara.edu.in/chitkara/chitkarauniversity.php?page=../etc/passwdNow this will step up one directory (to directory E ) and look for 'etc' but again it will return nothing.
Now type
http://www.chitkara.edu.in/chitkara/chitkarauniversity.php?page=../../etc/passwdNow this will step up two directories (to directory D ) and look for 'etc' but again it will return nothing.
So by proceeding like this, we we go for this URL
http://www.chitkara.edu.in/chitkara/chitkarauniversity.php?page=../../../../../etc/passwd
It takes us 5 directories up to the main drive and then to 'etc' directory and show us contents of 'passwd' file.
To understand the contents of 'passwd' file, visit http://www.cyberciti.biz/faq/understanding-etcpasswd-file-format
You can also view etc/profile ,etc/services and many others files like backup files which may contain sensitive data. Some files like etc/shadow may be not be accessible because they are accesible only by privileged users.
Note- If proc/self/environ would be accessible, you might upload a shell on server which is called as Local File Inclusion.
Counter Measures
1. Use the latest web server software
2. Effectively filter the user's input
Friday, September 24, 2010
Metasploit Explained for Beginners!
Metaspoit Framework is a open source penetration tool used for developing and executing exploit code against a remote target machine it, Metasploit frame work has the world's largest database of public, tested exploits. In simple words, Metasploit can be used to test the vulnerability of computer systems in order to protect them and on the other hand it can alsobe used to break into remote systems.
Its a powerful tool used for penetration testing. Learning to work with metasploit needs a lot of efforts and time. Ofcourse to can learn metasploit overnight, it needs lots of practice and patience
Download here(windows user)
http://www.metasploit.com/releases/framework-3.2.exe
Download here(linux user)
http://www.metasploit.com/releases/framework-3.2.tar.gz
Just give a look at following basic steps for beginners to break into a system using metasploit after gathering some information about the target system.
1. Select a right exploit and then set the target.
2.Verify the exploit options to determine whether the target system is vulnerable to the exploit.
3.Select a payload
4.Execute the exploit.
You must be confused !!!!
Now carefully read the following basic terms to get an idea about these four steps mentioned above .I have defined the terms technically and side by side explained in layman language to clarify the things. I have taken an example that an attacker wants to break into a house . I hope my this approach will give you a great idea about these basic terms .
Like the main gate of house with a weak lock (can be easily opened) , a glass window of house(can be easily broken) etc can be the vulnerabilities in the systems which make it easy for an attacker to break into.
The set of different keys which he can try one by one to open the lock , the hammer with him which he can use to break the glass window etc can be the exploits.
Now Finally after exploiting the vulnerability and breaking in , he can have different things to do. He can steal money, destroy the things or just can give a look and come back.. Deciding this is what we mean by setting the Payload.
I hope its enough friends, You will learn more with further tutorials when you will start working with metasploit practically.
About The Author
This is a guest post written by Aneesh M Makker. Aneesh M.Makker is an Ethical hacker from Malout, a town in Punjab.Click here to visit his Facebook Profile
Its a powerful tool used for penetration testing. Learning to work with metasploit needs a lot of efforts and time. Ofcourse to can learn metasploit overnight, it needs lots of practice and patience
Download here(windows user)
http://www.metasploit.com/releases/framework-3.2.exe
Download here(linux user)
http://www.metasploit.com/releases/framework-3.2.tar.gz
Just give a look at following basic steps for beginners to break into a system using metasploit after gathering some information about the target system.
1. Select a right exploit and then set the target.
2.Verify the exploit options to determine whether the target system is vulnerable to the exploit.
3.Select a payload
4.Execute the exploit.
You must be confused !!!!
Now carefully read the following basic terms to get an idea about these four steps mentioned above .I have defined the terms technically and side by side explained in layman language to clarify the things. I have taken an example that an attacker wants to break into a house . I hope my this approach will give you a great idea about these basic terms .
Vulnerability -A weakness which allows an attacker to break into or compromise a system's security.
Like the main gate of house with a weak lock (can be easily opened) , a glass window of house(can be easily broken) etc can be the vulnerabilities in the systems which make it easy for an attacker to break into.
Exploit - Code which allows an attacker to take advantage of a vulnerability system.
The set of different keys which he can try one by one to open the lock , the hammer with him which he can use to break the glass window etc can be the exploits.
Payload- Actual code which runs on the system after exploitation
Now Finally after exploiting the vulnerability and breaking in , he can have different things to do. He can steal money, destroy the things or just can give a look and come back.. Deciding this is what we mean by setting the Payload.
I hope its enough friends, You will learn more with further tutorials when you will start working with metasploit practically.
About The Author
This is a guest post written by Aneesh M Makker. Aneesh M.Makker is an Ethical hacker from Malout, a town in Punjab.Click here to visit his Facebook Profile
Thursday, September 23, 2010
How To Spy and Hack a webcam
Gone are those days when webcam Hacking was a sophisticated art now a days any one with very basic knowledge of computers can start to Hack your webcam, from last couple of months I was getting asked by readers "How To spy a webcam?" or "How to Hack a webcam?", So I decided to write a post on this topic and tell you how Hackers manage to spy a webcam
Most of the hackers use some spying softwares like RAT's, which are used to gain physical access to victims computer, Once a RAT(Remote Administration Tool) is installed in to victims computer you can easily do almost any thing with his/her computer and also spy on his/her webcam, but at the same time RAT's have some disadvantages as well
1. RAT's are easily detected by almost every antivirus and thus it will delete it before executing, Skilled hackers use some methods to hide antivirus detection of RAT's such as Hexing, File pumping, crypting etc but they are not easy and not recommended for beginners
2. The other problem with RAT's is that you can be easily traced back
3. You can your self get infected while playing with RAT's
After looking at the above disadvantages of RAT's I think that they are of no use, You might be thinking that how in the world hackers hack webcam now ,You need not to worry as I will show you three superb tool which can get the job done for you, even if you have a very little knowledge of operating systems
Web spy hack is one of the most cheapest solution for those who want to monitor any webcam, The software costs 14$ only and is totally worth the money
Below are some features of web spy hack
Winspy keylogger is a Complete Stealth Monitoring Package that can spy on both your Local PC and Remote PC. It includes Remote Install and Realtime Remote PC Viewer. Win Spy Software will capture anything the user sees or types on the keyboard. A special hotkey is used to login and access the program. Users will not be able to terminate or uninstall Win-Spy.
Win-Spy Software operates in stealth mode. It will not appear in Windows Start, System Tray, Desktop, Task Manager or Add/Remove Programs.
Win Spy Features
1. Monitor Chat Room (dual side) and web activity
2. Remote Monitor any Email
3. Remote Monitor children’s activity on any PC
4. Records any Password (Email, Login, Instant Messenger etc.)
5. Monitor Remote PC Webcam
For more information on this program and download details visit the following link
Win Spy Download
Which is best Web spy hack or winspy?
Well it depends upon you, If you are looking for a cheaper solution I suggest you to go Web spy hack and if you have just little extra money and are looking for a better spy software I suggest you to go for winspy then
Most of the hackers use some spying softwares like RAT's, which are used to gain physical access to victims computer, Once a RAT(Remote Administration Tool) is installed in to victims computer you can easily do almost any thing with his/her computer and also spy on his/her webcam, but at the same time RAT's have some disadvantages as well
1. RAT's are easily detected by almost every antivirus and thus it will delete it before executing, Skilled hackers use some methods to hide antivirus detection of RAT's such as Hexing, File pumping, crypting etc but they are not easy and not recommended for beginners
2. The other problem with RAT's is that you can be easily traced back
3. You can your self get infected while playing with RAT's
After looking at the above disadvantages of RAT's I think that they are of no use, You might be thinking that how in the world hackers hack webcam now ,You need not to worry as I will show you three superb tool which can get the job done for you, even if you have a very little knowledge of operating systems
Webcam Spying Tools
Here are few webcam Hacking tools which I recommend:Web spy hack
Update: The program is no longer available due to violation of clickbanks terms and conditions.
Below are some features of web spy hack
- Access almost any computer anywhere without knowing the computer password or IP Address.
- Record and watch any webcam at the same time.
- Record desktop action and watch at the same time.
- Dig deep into files, download then and upload new ones.
- Watch a webcam from any PC in the world.
- Monitor activities whenever that PC or laptop is online.
- Save all recordings in a number of file types.
Winspy keylogger
winspy is the best webcam monitoring software but if you are looking for a cheaper solution I suggest you should go for Web spy hackWinspy keylogger is a Complete Stealth Monitoring Package that can spy on both your Local PC and Remote PC. It includes Remote Install and Realtime Remote PC Viewer. Win Spy Software will capture anything the user sees or types on the keyboard. A special hotkey is used to login and access the program. Users will not be able to terminate or uninstall Win-Spy.
Win-Spy Software operates in stealth mode. It will not appear in Windows Start, System Tray, Desktop, Task Manager or Add/Remove Programs.
Win Spy Features
1. Monitor Chat Room (dual side) and web activity
2. Remote Monitor any Email
3. Remote Monitor children’s activity on any PC
4. Records any Password (Email, Login, Instant Messenger etc.)
5. Monitor Remote PC Webcam
For more information on this program and download details visit the following link
Win Spy Download
Which is best Web spy hack or winspy?
Well it depends upon you, If you are looking for a cheaper solution I suggest you to go Web spy hack and if you have just little extra money and are looking for a better spy software I suggest you to go for winspy then
Monday, September 20, 2010
How to use sniperspy to hack passwords
1.How can i use Sniperspy for email hacking?
2.Is my order 100% safe?
3.If i dont Have phisical acess to victims computer can i still install sniperspy?
4.Will the victim know about it if i install sniperspy?
5.Which is best Sniperspy or Winspy?
6.What do i do if Antivirus catch me ?
7.Can i be traced Back if i install it on someones computer?
Sniperspy FAQ
How can i Use Sniperspy for email hacking?
Its very easy to use sniperspy,a person with basic knowledge of computer can use and operate sniperspy:
1.First you need to purchase sniperspy.
2.After the order is complete, you will be instantly emailed a receipt with your Username/Password and a link to download the Module Creator program. You will download this program to your local computer in order to create the module to send to your remote computer.
3. Run the module creator program and enter your Username/Password into the fields. Then follow the screens to adjust the settings to your needs. Once the module wizard is finished, your module EXE file will be created in the location and name you selected. Some people choose unique names for the module such as funpics.exe or Anything.exe.
4.Once you have got sniperspy installed into victims Computer,you will receive logs,screenshots etc over periods,You can login into your sniperspy account to see the screen shots,logs and email passwords
Is my Order 100% safe?
Yes.All orders of Sniperspy are handled by plimus which is a very well known and popular company.The privacy and protection of your online order is 100% safe.you can give order with worrying about scams
Will the victim know about it if i install sniperspy?
No.Its almost impossible to know about it,because once sniperspy is installed into victims computer it runs in a total stealth mode,it hides it self from Startup,taskmanager add/remove program and Program files.
What do i do if Antivirus catch me ?
If you are afraid that antivirus might catch you than read my post on How to bypass antivirus detection of keylogger
Can i be traced Back if i install it on someones computer?
No.Its almost impossible to be traced back if you install sniperspy on someones computer
If i dont Have phisical acess to victims computer can i still install sniperspy?
Yes.You do not need physical access into victims computer to install a sniperspy or winspy you just need to make victim install a small remote file after which you will be recieve password,screenshots,logs etc over periods
Which is Best sniperspy or winspy?
I recommend Sniperspy for the following reasons:
1.Sniperspy is Fully compatible with windows vista,but winspy has known compatible issues with Windows vista
2.It has low antivirus detection rate
3.It can bypass firewall
4.Sniperspy is recognized by CNN,BBC,CBS and other popular news network,Hence it is reputed and trustworthy
Sniperspy is completely reliable and user-friendly,It is worth price that you pay for it,you cannot get a better keylogger than this,So what are you waiting for?Go grab the Sniperspy now
Click Here to Order SniperSpy Now!
Note:Installing computer monitoring tools on computers you do not own or do not have permission to monitor may violate local, state or federal law.
Sunday, September 19, 2010
How to hide sensitive data - Steganography
There are many ways we hide our data in computer some people use encryption tools like Truecrypt, some hide there files in folders , some use folder lock etc.”Steganography “ ,I cannot say it as a new concept but it different from others(mentioned above)and has a wide range of application. Here I will discuss few basics aspects of this technique with few freeware tools for Windows OS available online
What is Steganography?
It is the art of hiding data or message in another file invisible to a targeted mass of people. Mostly people have a wrong concept that steganography is related to images only i.e. hiding messages in images only but actually that is not the case it can be done in other file formats also .We can also hide .RAR file in .DOCX formats etc.Carrier file(Size:23kb) + Message = Stego File(Size:More than 23kb)
As mentioned above “Carrier file” is the file where we can hide the message or data, after that as you can see above the size of the file has increased .
Applications of Steganography
- This techniques is believed to be used by terrorists for sending confidential messages.
- Used by intelligence agencies for sending confidential data.
- Used by some website owners for marking their images.
- Used in digital water marking images.
- Used in laser printers for hiding the serial no of printers.
Procedure:
Here I will use few tools and commands to demonstrate the basics of steganographyMethod 1
Step 1.Open up command prompt from the start button on the taskbar.
Step 2
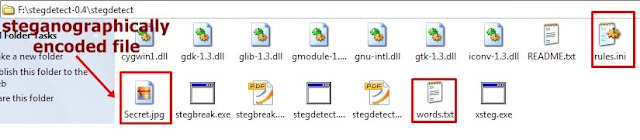
Suppose you have an image file Compufreaks.jpg (carrier file) and you want to hide a file called RHA.rar(message) in that.
Step 3.
You have to keep both the files in the same folder and change the path of the drive to that folder in command prompt.
Step 4
Then use the command ”copy /b Compufreaks.jpeg+RHA.rar Secret.jpeg “ and check the size of the files as shown below, now you have sucessfully hided computerfreaks.jpeg in to RHA.rar
Method 2
The tools we will be using here isStep 1.
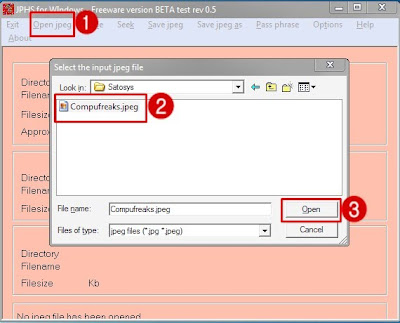
Having downloaded the required files open up Jphs_0.5.(click on Jphswin.exe) in the extracted folder.
Step2.
Click on the “open jpeg” on the top menu and browse to find the required file and click open.
Step 3.
Now click on hide on the top and enter the password then click ok to select the required message file and save it.
How to Detect Hidden messages?
The method of detection of hidden message in a steganographically encoded file is known as Steganalysis.Here I will bring out few of the basic techniques of steganalysis.
Requirements
a) Stegdetect_0.4
b) Wordlist file
c) Rules.ini file
Method 1
Step 1.Once you have downloaded the required file , now open up command prompt and change the path where you have downloaded Stegdetect_0.4(extracted).
Step 2.
Now put the required steganographically encoded file(Secret.jpg) generated from method 2.above in that folder where you have exracted Stegdetect_0.4.
Step 3
In the command prompt use the command stegdetect –t p secret.jpg and hit enter,then it will show the show the steganography tool used and password as <******>.
Step 4.
Now use the command stegbreak –r rules.ini –f words.txt –t p secrect.jpg and hit enter it will show the password and no . of embeddings.
Note:Always use the extension of the required file in the above command.
Step 5.
Having know the password open the file using Jphs_0.5 and then click seek on the top menu use the password (retrieved above) and save the file in the format of the data file.
Method 2
There is an online tool available called Mozaiq which does all the work that I described in method 1. above.Then you can use Mozaiq Decrypt for decrypting the steganographically encrypted file .
Certianly steganography is really a vast topic of discussion ,here I have tried to bring out few essential aspects of it .Hope you like it.
If you find this article worth reading then do drop a comment,it will be appreciated.
About The Author
This article is written by Satyajit Das. He writes at his Blog Security Hunk, where he writes related to computer security. If you are interested in writting a guest post on your blog kindly read the guidelines here
Saturday, September 18, 2010
Cracking FTP Passwords Using Dictionary Attacks
What is a Dictionary Attack ?
In layman language, Dictionary attack means using a tool that picks passwords from a wordlist and tries them one by one until one works
How to make a wordlist ?
A wordlist can consist of all possible combinations of letter,numbers,special characters. It can have some common or default passwords. You can download the wordlist generators or google the wordlists for bruteforcing and configure them according to yourself.
How fruitful attack can be ?
If we are try all possible combinations of letter,numbers,special characters, theoretically chances of success are 100%. But practically it is not possible to try every combination because it can take a lot of time. This attack just depends on the time you give,processing power and ofcourse your luck.
Tool I will be using ?
Step 1
Download THC Hydra from here
Step 2
(a) Make a usename wordlist consisting of some common usernames like this
(b) Get a wordlist of passwords
(c) Copy both wordlists to your hydra folder
Step 3
(a)Open the command prompt and change directory to your hydra folder using cd command.
(b) Type "hydra" without quotes and it will show you the options to use.
(c) Now to start attak,
Type "hydra -L userslist.txt -P passlist.txt xxx.xxx.xxx.xxx ftp" and press enter
where userslist.txt is the list of usernames, passlist.txt is the list of passwords and xxx.xxx.xxx.xxx is the IP address of target, Now it will start cracking
To use a single username instead of wordlist , Replace capital L with small l , like this
Type "hydra -l username -P passlist.txt xxx.xxx.xxx.xxx ftp"
Note : Ftp port must be open.
Warning: I highly recommend you to use a chain of proxies to spoof your identity because proper logs of user's IP addresses who try to connect to ftp server is made on the server. Here is an example of the same.
Countermeasures to protect yourself from this attack:
1. Use strong passwords
2. Enable Autoban of IPs or anyother option like this.
About The Author
This is a guest post written by Aneesh M Makker. Aneesh M.Makker is an Ethical hacker from Malout, a town in Punjab.Click here to visit his Facebook Profile
In layman language, Dictionary attack means using a tool that picks passwords from a wordlist and tries them one by one until one works
How to make a wordlist ?
A wordlist can consist of all possible combinations of letter,numbers,special characters. It can have some common or default passwords. You can download the wordlist generators or google the wordlists for bruteforcing and configure them according to yourself.
How fruitful attack can be ?
If we are try all possible combinations of letter,numbers,special characters, theoretically chances of success are 100%. But practically it is not possible to try every combination because it can take a lot of time. This attack just depends on the time you give,processing power and ofcourse your luck.
Tool I will be using ?
- THC Hydra
Step 1
Download THC Hydra from here
Step 2
(a) Make a usename wordlist consisting of some common usernames like this
(b) Get a wordlist of passwords
(c) Copy both wordlists to your hydra folder
Step 3
(a)Open the command prompt and change directory to your hydra folder using cd command.
(b) Type "hydra" without quotes and it will show you the options to use.
(c) Now to start attak,
Type "hydra -L userslist.txt -P passlist.txt xxx.xxx.xxx.xxx ftp" and press enter
where userslist.txt is the list of usernames, passlist.txt is the list of passwords and xxx.xxx.xxx.xxx is the IP address of target, Now it will start cracking
To use a single username instead of wordlist , Replace capital L with small l , like this
Type "hydra -l username -P passlist.txt xxx.xxx.xxx.xxx ftp"
Note : Ftp port must be open.
Warning: I highly recommend you to use a chain of proxies to spoof your identity because proper logs of user's IP addresses who try to connect to ftp server is made on the server. Here is an example of the same.
Countermeasures to protect yourself from this attack:
1. Use strong passwords
2. Enable Autoban of IPs or anyother option like this.
About The Author
This is a guest post written by Aneesh M Makker. Aneesh M.Makker is an Ethical hacker from Malout, a town in Punjab.Click here to visit his Facebook Profile
Thursday, September 16, 2010
Write for us
Are you tired of trying foolish methods to get traffic to your blog?, Do you want to build high Pr quality backlinks to your blog?, then you need to not to worry as RHA has started to accept guest posts on their blog.RHA is a PR 4 blog with 14k+ RSS subscribers and is updated regularly, By writting on RHA you can get lot of exposure and traffic to your blog or website and at the same time built quality backlinks to your blog
Requirements
- Proper and original content
- Related to security/hacking
- Proper grammar
What well will give you in return?
- A link to your website on the post
- And depending on how much and how many times you contribute, you may get free access to some of my upcoming hacking products
Rafay Hacking Articles Re Designed
Hi Readers I am Very Happy to announce you that finally after huge request of readers and with the grace of Almighty Allah I have successfully changed my blog Theme,The theme is designed by one of the finest designers of karachi Pakistan Mohammad Mustafa Ahmedzai he has named this theme as "Cracker"
The previous design of this blog was very unprofessional as suggested by many of designers and looked something like this:
As you can see that the design was very unprofessional and due to that I had a high bounce rate and less page loads, As soon as I changed the design the page views turned for 1.5 pages/user to 2.0 pages/ user
2) Customized Comment Form and Comment Interface
3) A Flapping Social Bookmarking Widget Below Post body with MBT's copyrighted Icons
4) Bookmark and Share widget Near Navigation Menu
5) Stylized Subscription Form
6) Customized Profile Widget
7) Powerful Header And Navigation
The header was designed by Mustafa and Its designed very professionally, The Navigation menu is user friendly and eye catching
8) Optimized Commenting System
Mustafa was the first person who desgined a hack to style comment form, The new comment form looks awesome and optimized
The whole theme cost me 200$ and I think its worth the price, Mohammad Mustafa Ahmedzai blogs on Mybloggertricks feel free to express your feeling on this blog, What things did you like? and what things you did not like? what changes can make the theme better?, I want your honest opinions on this theme
The previous design of this blog was very unprofessional as suggested by many of designers and looked something like this:
As you can see that the design was very unprofessional and due to that I had a high bounce rate and less page loads, As soon as I changed the design the page views turned for 1.5 pages/user to 2.0 pages/ user
Features of the new Theme
1) Eye Catching Header and Highly user friendly Navigation Menu2) Customized Comment Form and Comment Interface
3) A Flapping Social Bookmarking Widget Below Post body with MBT's copyrighted Icons
4) Bookmark and Share widget Near Navigation Menu
5) Stylized Subscription Form
6) Customized Profile Widget
7) Powerful Header And Navigation
The header was designed by Mustafa and Its designed very professionally, The Navigation menu is user friendly and eye catching
8) Optimized Commenting System
Mustafa was the first person who desgined a hack to style comment form, The new comment form looks awesome and optimized
The whole theme cost me 200$ and I think its worth the price, Mohammad Mustafa Ahmedzai blogs on Mybloggertricks feel free to express your feeling on this blog, What things did you like? and what things you did not like? what changes can make the theme better?, I want your honest opinions on this theme
Tuesday, September 14, 2010
How to trace a sender's information in Gmail?
Now a days email spoofing has been a very common act, there are tons of softwares which can be used for email spoofing. Alot of scammers use mail bombing along with email spoofing, As you know that this blog is for beginners so i will first explain what is mail bombing? and what is email spoofing? and then will explain you How to trace a sender in Gmail!
Email spoofing is an act to sent an email from an email which does not belong to you, this is mostly used for scamming people, Hackers use it as a medium for social engineering
For Example If a user gets a phishing scam asking to update his login information, the senders email is something like xyz@hotmail.com, this would make the victim suspicious and he/she will not pay attention to this email but on the other hand if the email is from security@microsoft.com or security@facebook.com the victim would probably feel that the email is from real sender and he/she would give his login details
What is Mail bombing?
A Mail bombing is sending a mass number of emails to a specific person or system.A huge amount of mail may simply fill up the recipient's disk space on the server or, in some cases, may be too much for a server to handle and may cause the server to stop functioning
Combining Mail bombing with Email
A few days back when I opened my Gmail ID, I noticed that i had received 5000+ emails those all emails looked that they were from different senders as each email's body was same but the email addresses keep changing.
For example: The first email will be 1234@attacker.com the others numbers before @ would change in every email.
I was receiving 100+ emails per second, A normal user would create a spam filter for one of the email 1234@attacker.com but this wont stop the attack as the email 1234@attacker.com is the spoofed email not the real email, so here is how I traced the sender's information in Gmail
Tracing a Senders information in Gmail
You must be curious to know that how I traced senders information in gmail, some of you might ask how to trace sender's information in Hotmail or Yahoo, so I will explain it in upcoming articles in my blog as these are not the part of the article
Here is the step by step method to trace a sender's information in Gmail
1.Open the Email in Gmail you want to trace
2.Click on More Options and Click on “Show originals”
Refer to Image for More details:
3. Now a new Window will pop up like this and there see the highlighted area
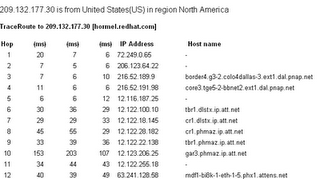
4. Check the first line “hormel.redhat.net” ip=209.132.177.30″
That’s The Ip of The sender. now to trace the sender using this ip.
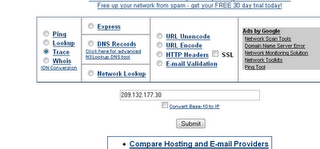
5. Open this site www.network-tools.com
Enter the IP address and click on submit
Hope you have liked the article to trace a sender's information in Gmail, If you have any problem or quesion regarding any thing in the article feel free to ask me!
What is Email Spoofing?
Email spoofing is an act to sent an email from an email which does not belong to you, this is mostly used for scamming people, Hackers use it as a medium for social engineering
For Example If a user gets a phishing scam asking to update his login information, the senders email is something like xyz@hotmail.com, this would make the victim suspicious and he/she will not pay attention to this email but on the other hand if the email is from security@microsoft.com or security@facebook.com the victim would probably feel that the email is from real sender and he/she would give his login details
What is Mail bombing?
A Mail bombing is sending a mass number of emails to a specific person or system.A huge amount of mail may simply fill up the recipient's disk space on the server or, in some cases, may be too much for a server to handle and may cause the server to stop functioning
Combining Mail bombing with Email
A few days back when I opened my Gmail ID, I noticed that i had received 5000+ emails those all emails looked that they were from different senders as each email's body was same but the email addresses keep changing.
For example: The first email will be 1234@attacker.com the others numbers before @ would change in every email.
I was receiving 100+ emails per second, A normal user would create a spam filter for one of the email 1234@attacker.com but this wont stop the attack as the email 1234@attacker.com is the spoofed email not the real email, so here is how I traced the sender's information in Gmail
Tracing a Senders information in Gmail
You must be curious to know that how I traced senders information in gmail, some of you might ask how to trace sender's information in Hotmail or Yahoo, so I will explain it in upcoming articles in my blog as these are not the part of the article
Here is the step by step method to trace a sender's information in Gmail
1.Open the Email in Gmail you want to trace
2.Click on More Options and Click on “Show originals”
Refer to Image for More details:
3. Now a new Window will pop up like this and there see the highlighted area
4. Check the first line “hormel.redhat.net” ip=209.132.177.30″
That’s The Ip of The sender. now to trace the sender using this ip.
5. Open this site www.network-tools.com
Enter the IP address and click on submit
Hope you have liked the article to trace a sender's information in Gmail, If you have any problem or quesion regarding any thing in the article feel free to ask me!
Saturday, September 11, 2010
How to hack yahoo messenger password

Everyday I get a lot of emails from people asking How to hack a Yahoo password? So if you’re curious to know how to hack a yahoo password then this is the post for you. In this post I will give you the real and working ways to hack Yahoo password.
There are number of sites on the web that provide information to hack a Yahoo password. So what’s special about this site? The only special about this site is that we do not bluff and mislead the readers. We actually teach you the real and working ways to hack a Yahoo password rather than telling some nonsense tricks to crack or hack some one’s yahoo password.
Using keylogger is the easiest way to hack a Yahoo messenger password. Any one with a basic knowledge of computer can use a keylogger without any problems. It doesn’t matter whether or not you’ve physical access to the target computer. The following are some of the frequently asked questions about keyloggers.
1. What is a keylogger?
A keylogger is a small program that records each and every keystroke (including passwords) that a user types on a specific computer’s keyboard. A keylogger is also called as Spy program or Spy software.
2. Where can I get the keylogger?
There exists hundrends of keyloggers on the internet. But most of them are of poor quality and fail to deliver a good performance. The two best keyloggers for hacking yahoo password are listed below.
1.SniperSpy (Supports Remote Installation)
2.Win-Spy (Supports Remote Installation)
3. Which keylogger is the best to hack Yahoo password?
Both the above mentioned ones are best for hacking Yahoo. However I recommend Sniperspy since it is more reliable and has got a better advantage over Winspy.
If you’re really serious to hack a Yahoo password then I strongly recommend using either of the two mentioned keyloggers.
OTHER WAYS TO HACK YAHOO PASSWORD
The other most commonly used trick to hack Yahoo password is using a Fake Login Page (also called as Phishing). Today, Fake login pages are the most widely used techniques to hack Yahoo password. A Fake Login page is a page that appears exactly as a Login page of sites like Yahoo, Gmail etc. But once we enter our password there, we end up loosing it.
Fake login pages are created by many hackers on their sites which appear exactly as Gmail or Yahoo login pages but the entered details(username & password) are redirected to remote server and we get redirected to some other page. Many times we ignore this but finally we loose our valuable data.
However creating a fake login page and taking it online to successfully hack a Yahoo password is not an easy job. It demands an in depth technical knowledge of HTML and scripting languages like PHP, JSP etc. So if you are new to the concept of hacking passwords, then I recommend using the keyloggers to hack Yahoo. Because Keyloggers are the easiest way to hack Yahoo password.
I have made a post on Hack yahoo using fake login page,kindly check it out
Tuesday, September 7, 2010
What is Social Enginering in the field of Hacking?
Social engineering is defined as the process of obtaining others passwords or personal information by the act of manipulating people rather than by breaking in or using technical cracking techniques. Here I will show you an example on how social engineering works
Example 1
Robert (Hacker) calls Michael and pretends to be a Google employee, Here is the
conversation:
Robert: Hi Michael I am Robert a Google employee
Michael: OH How are you doing?
Robert: Me fine. I am here to inform you that Google is performing a security update on all Google accounts and we therefore need to install those securities updates on
your account.
Michael: Yes kindly install those security updates.
Robert: Thanks for your interest in our security updates we will require your account
password for installing it.
Michael (Victim) has become a victim of social engineering, he will give out his password thinking that the person whom he was chatting was a Google employee.
Note: The Hacker will create an account similar to
Googleupdates(at)gmail.com
Securityupdates(at)gmail.com
Example 2
You may receive an email from saying that your computer is infected with virus and to eliminate this virus you need to install a tool. The tool will not eliminate virus from your computer but instead it will give access to your computer and all data stored on
it.
Remember: Never give out details, or secure information such as your passwords. Use passwords that aren’t anything to do with your age/DOB/FirstName/Surname etc. All of that can be found too easily.
This article was a part of my book A Beginners Guide To Ethical Hacking, if you are a beginner and want to Learn Ethical hacking I suggest you to purchase a copy of my book
Example 1
Robert (Hacker) calls Michael and pretends to be a Google employee, Here is the
conversation:
Robert: Hi Michael I am Robert a Google employee
Michael: OH How are you doing?
Robert: Me fine. I am here to inform you that Google is performing a security update on all Google accounts and we therefore need to install those securities updates on
your account.
Michael: Yes kindly install those security updates.
Robert: Thanks for your interest in our security updates we will require your account
password for installing it.
Michael (Victim) has become a victim of social engineering, he will give out his password thinking that the person whom he was chatting was a Google employee.
Note: The Hacker will create an account similar to
Googleupdates(at)gmail.com
Securityupdates(at)gmail.com
Example 2
You may receive an email from saying that your computer is infected with virus and to eliminate this virus you need to install a tool. The tool will not eliminate virus from your computer but instead it will give access to your computer and all data stored on
it.
Remember: Never give out details, or secure information such as your passwords. Use passwords that aren’t anything to do with your age/DOB/FirstName/Surname etc. All of that can be found too easily.
This article was a part of my book A Beginners Guide To Ethical Hacking, if you are a beginner and want to Learn Ethical hacking I suggest you to purchase a copy of my book
Friday, September 3, 2010
Adobe Photoshop CS5 Serial Numbers
Adobe Photoshop CS5 is the latest version of photoshop.Adobe Photoshop CS5 is the industry-standard image editing software, used worldwide by professional photographers and designers who want to perfect their digital images, but due to its high price a very few number of people can afford it
Previously I wrote an article on Adobe Photoshop CS5 keygen, however some of readers had problems and faced difficulties in downloading them so in this article I will be posting Adobe CS5 Serial Numbers.
Here are a Few working Adobe Photoshop CS5 Serial Numbers
Update:Due to instructions by our advertising network I have removed the keys from this post.
However you can download them here
You can also Download Adobe CS5 100% working Keygen if the above codes do not work for you
Subscribe to:
Comments (Atom)