There are many ways we hide our data in computer some people use encryption tools like Truecrypt, some hide there files in folders , some use folder lock etc.”Steganography “ ,I cannot say it as a new concept but it different from others(mentioned above)and has a wide range of application. Here I will discuss few basics aspects of this technique with few freeware tools for Windows OS available online
What is Steganography?
It is the art of hiding data or message in another file invisible to a targeted mass of people. Mostly people have a wrong concept that steganography is related to images only i.e. hiding messages in images only but actually that is not the case it can be done in other file formats also .We can also hide .RAR file in .DOCX formats etc.Carrier file(Size:23kb) + Message = Stego File(Size:More than 23kb)
As mentioned above “Carrier file” is the file where we can hide the message or data, after that as you can see above the size of the file has increased .
Applications of Steganography
- This techniques is believed to be used by terrorists for sending confidential messages.
- Used by intelligence agencies for sending confidential data.
- Used by some website owners for marking their images.
- Used in digital water marking images.
- Used in laser printers for hiding the serial no of printers.
Procedure:
Here I will use few tools and commands to demonstrate the basics of steganographyMethod 1
Step 1.Open up command prompt from the start button on the taskbar.
Step 2
Suppose you have an image file Compufreaks.jpg (carrier file) and you want to hide a file called RHA.rar(message) in that.
Step 3.
You have to keep both the files in the same folder and change the path of the drive to that folder in command prompt.
Step 4
Then use the command ”copy /b Compufreaks.jpeg+RHA.rar Secret.jpeg “ and check the size of the files as shown below, now you have sucessfully hided computerfreaks.jpeg in to RHA.rar
Method 2
The tools we will be using here isStep 1.
Having downloaded the required files open up Jphs_0.5.(click on Jphswin.exe) in the extracted folder.
Step2.
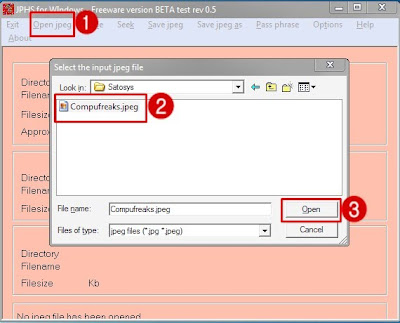
Click on the “open jpeg” on the top menu and browse to find the required file and click open.
Step 3.
Now click on hide on the top and enter the password then click ok to select the required message file and save it.
How to Detect Hidden messages?
The method of detection of hidden message in a steganographically encoded file is known as Steganalysis.Here I will bring out few of the basic techniques of steganalysis.
Requirements
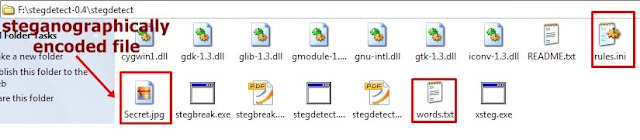
a) Stegdetect_0.4
b) Wordlist file
c) Rules.ini file
Method 1
Step 1.Once you have downloaded the required file , now open up command prompt and change the path where you have downloaded Stegdetect_0.4(extracted).
Step 2.
Now put the required steganographically encoded file(Secret.jpg) generated from method 2.above in that folder where you have exracted Stegdetect_0.4.
Step 3
In the command prompt use the command stegdetect –t p secret.jpg and hit enter,then it will show the show the steganography tool used and password as <******>.
Step 4.
Now use the command stegbreak –r rules.ini –f words.txt –t p secrect.jpg and hit enter it will show the password and no . of embeddings.
Note:Always use the extension of the required file in the above command.
Step 5.
Having know the password open the file using Jphs_0.5 and then click seek on the top menu use the password (retrieved above) and save the file in the format of the data file.
Method 2
There is an online tool available called Mozaiq which does all the work that I described in method 1. above.Then you can use Mozaiq Decrypt for decrypting the steganographically encrypted file .
Certianly steganography is really a vast topic of discussion ,here I have tried to bring out few essential aspects of it .Hope you like it.
If you find this article worth reading then do drop a comment,it will be appreciated.
About The Author
This article is written by Satyajit Das. He writes at his Blog Security Hunk, where he writes related to computer security. If you are interested in writting a guest post on your blog kindly read the guidelines here











No comments:
Post a Comment